Suite Definition
The BabyJubjub 2021 signature suite MUST be used in conjunction with the signing and verification algorithms in the Linked Data Signatures [[LD-SIGNATURES]] specification. The suite consists of the following algorithms:
| Parameter | Value | Specification |
|---|---|---|
| canonicalizationAlgorithm | https://w3id.org/security#URDNA2015 | [[RDF-DATASET-NORMALIZATION]] |
| digestAlgorithm | Poseidon | [[GKR+19]] |
| signatureAlgorithm | EdDSA-BabyJubJub | [[BB19]] |
Modification to Algorithms
The hash function in the signature algorithm has been repleaced to Poseidon[[GKR+19]] hash function.
Document Merklization Algorithm
The signature suite incorporates a Document Merkleization algorithm to provide enhanced zero-knowledge compatibility support. This feature enables efficient querying of individual entries within JSON-LD documents in the context of zk-SNARK proofs. By constructing a Sparse Merkle Tree from the document, the algorithm supports selective disclosure of Verifiable Credential (VC) entries, efficiently prove membership, non-membership, and other predicate satisfactions related to the JSON-LD document, while maintaining the privacy and integrity of the data.
Prior to applying the Merkleization algorithm, the document must be in its expanded and canonicalized form.
The Merklization algorithm works as follow:
- Obtain a list of RDF Quads from the canonicalized document.
- For each Quad, construct a key-value pair where the key represents the complete type path, and the value corresponds to the entry's value.
- Insert each key-value pair into the Merkle Tree, with the key serving as the path in the tree and the leaf's value being the hash of the pair's value, computed using the designated message digest algorithm.
- For each key-value pair, first hash the key using the designated message digest algorithm, and use the hashed key as the path in the Merkle Tree. Then, hash the value using the same message digest algorithm, and set the resulting hash as the value of the corresponding leaf node in the tree.
For a detailed illustration of the Merkleization algorithm applied to a JSON-LD document, please refer to the example provided in the Examples section of this document.
Selective Disclosure
To better comprehend how the signature suite enables selective disclosure, let us examine the underlying mechanism. In this process, a credential undergoes Merkleization, during which each entry of the document is stored in a leaf. Subsequently, the root is signed by the issuer. To facilitate selective disclosure, the prover can share the following information with the verifier:
- The root of the Merkleized credential.
- The issuer's signature on the root.
- The relevant authentication paths for the selectively disclosed entries.
BJJSignature2021
All verifiable credentials issued with the BabyJubjub 2021 signature suite must include a proof object with "BJJSignature2021" as the proof type. The BJJSignature2021 proof contains the issuer's data, the core claim, and a signature created using the issuer's private key. The following example demonstrates a BJJSignature2021 proof:
{
"type": "BJJSignature2021",
"issuerData": {
"id": "did:iden3:polygon:wz7EXpsG9jdQC4edi3kyXC5SroZfqbcPKTYaJc5t6",
...
},
"coreClaim": "c9b2370371b7fa8b3dab2a5ba81b68382a00000000000000000000000000000001129e344820de5301d7ae7f88ba5143f4ab9a9506e82331ec7ae8b21a830d006059621a4a3ed91795fc7919557e41c793ddbe93a30bc970f005cc72f89760270000000000000000000000000000000000000000000000000000000000000000c913b95700000000281cdcdf0200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000",
"signature": "588a56edc9862e0c7e2dbddade2ab30a156a36ac491205e82c6c1c9dfb5cd82c3bb51070c25a7f34cebf732013f11ef2c48a7c2e7cf706ec305d25b1bccffa05"
}The proof contains the signature of the coreClaim which is a serialization of the whole VC document except for the proof. The signature is created using the issuer's private key.
Proof Generation
The BJJSignature2021 proof generation process follows a specific algorithm to ensure the integrity and authenticity of JSON-LD documents. The steps of the algorithm are as follows:
- Expand the JSON-LD document using the JSON-LD 1.1 Processing Algorithms.
- Canonicalize the document using the URDNA2015 algorithm [[RDF-DATASET-NORMALIZATION]].
- Apply the Document Merklization Algorithm to create a Merkle tree from the canonicalized document.
- Sign the root of the document's Merkle tree using the associated private key.
Iden3StateInfo2023
The Iden3StateInfo2023 object is defined in the issuer's DID document and holds essential information about the issuer's state, such as state roots and related data. This object plays a crucial role in the verification process of verifiable credentials.
{
"id": "did:polygonid:polygon:2qL4AhwQThPWJ8QH9mxH41CDgKj9chrHN92azh5wkx?state=f3ed43e7fa950d746331b143bf16eae2dd97a1876704cbb8c620913421ea2f12",
"type": "Iden3StateInfo2023",
"blockchainAccountId": "80001:0x134B1BE34911E39A8397ec6289782989729807a4",
"published": true,
"info": {
"id": "did:polygonid:polygon:2qL4AhwQThPWJ8QH9mxH41CDgKj9chrHN92azh5wkx",
"state": "f3ed43e7fa950d746331b143bf16eae2dd97a1876704cbb8c620913421ea2f12",
"replacedByState": "0000000000000000000000000000000000000000000000000000000000000000",
"createdAtTimestamp": "1677691329",
"replacedAtTimestamp": "0",
"createdAtBlock": "32582097",
"replacedAtBlock": "0"
},
"global": {
"root": "d5a1afd7dd885ca97493c29640c8d43bc1af1ce165186974a42ddddfdea4182d",
"replacedByRoot": "0000000000000000000000000000000000000000000000000000000000000000",
"createdAtTimestamp": "1677691329",
"replacedAtTimestamp": "0",
"createdAtBlock": "32582097",
"replacedAtBlock": "0"
}
}
The issuer stores their public key in the state tree. During the verification of the verifiable credential, the verifier must check that the public key used to sign the document has an authentication path from the root specified in the Iden3StateInfo2023 object in the DID document.
To see an example of Iden3StateInfo2023 object in a DID document, please refer to the example provided in the Examples section of this document.
Proof Verification
To verify the authenticity and integrity of a selectively disclosed credential, the following steps should be performed:
- Retrieve the issuer's DID document and locate the Iden3StateInfo2023 object containing the state root and other relevant information.
- Verify that the issuer's public key, which signed the document, has a valid authentication path from the state root specified in the Iden3StateInfo2023 object within the DID document.
- Obtain the root of the Merkleized credential, the issuer's signature on the root, and the relevant authentication paths for the selectively disclosed entries from the prover.
- Validate the issuer's signature on the VC root using the issuer's public key.
- Reconstruct the Merkle tree based on the selectively disclosed entries and their corresponding authentication paths.
- Ensure that the reconstructed Merkle tree's root matches the root provided by the prover, thereby confirming the integrity and authenticity of the selectively disclosed credential.
Security Considerations
When implementing the BabyJubjub 2021 Signature Suite, several security considerations must be taken into account to ensure the integrity, confidentiality, and availability of the system.
Key Management
Proper key management practices must be followed to ensure the security of private keys. This includes secure key generation, storage, and destruction. It is essential to protect private keys from unauthorized access, as the loss or compromise of a private key could lead to impersonation or unauthorized access to signed documents.
Cryptographic Algorithms
The security of the BabyJubjub 2021 Signature Suite is dependent on the underlying cryptographic algorithms (Poseidon hash function and BabyJubJub signature algorithm). It is crucial to ensure that the chosen algorithms have been thoroughly analyzed and deemed secure by the cryptographic community.
Document Merklization
The Merklization process should be carefully implemented and reviewed to ensure that it preserves the integrity of the document while allowing for efficient zero-knowledge proofs. Any vulnerabilities in the Merklization algorithm could compromise the integrity of the signed document or the privacy of the zkSNARK proofs.
Side Channel Attacks
Implementations of the BabyJubjub 2021 Signature Suite should be designed to be resistant to side-channel attacks. These attacks could involve timing, power consumption, or electromagnetic radiation analysis to extract secret information from the system. Proper countermeasures should be employed to prevent such attacks.
Examples
DID Document
{
"@context": [
"https://www.w3.org/ns/did/v1",
"https://schema.iden3.io/core/jsonld/auth.jsonld"
],
"id": "did:polygonid:polygon:2qL4AhwQThPWJ8QH9mxH41CDgKj9chrHN92azh5wkx",
"authentication": [
{
"id": "did:polygonid:polygon:2qL4AhwQThPWJ8QH9mxH41CDgKj9chrHN92azh5wkx?state=f3ed43e7fa950d746331b143bf16eae2dd97a1876704cbb8c620913421ea2f12",
"type": "Iden3StateInfo2023",
"blockchainAccountId": "80001:0x134B1BE34911E39A8397ec6289782989729807a4",
"published": true,
"info": {
"id": "did:polygonid:polygon:2qL4AhwQThPWJ8QH9mxH41CDgKj9chrHN92azh5wkx",
"state": "f3ed43e7fa950d746331b143bf16eae2dd97a1876704cbb8c620913421ea2f12",
"replacedByState": "0000000000000000000000000000000000000000000000000000000000000000",
"createdAtTimestamp": "1677691329",
"replacedAtTimestamp": "0",
"createdAtBlock": "32582097",
"replacedAtBlock": "0"
},
"global": {
"root": "d5a1afd7dd885ca97493c29640c8d43bc1af1ce165186974a42ddddfdea4182d",
"replacedByRoot": "0000000000000000000000000000000000000000000000000000000000000000",
"createdAtTimestamp": "1677691329",
"replacedAtTimestamp": "0",
"createdAtBlock": "32582097",
"replacedAtBlock": "0"
}
}
]
}Document Merkleization
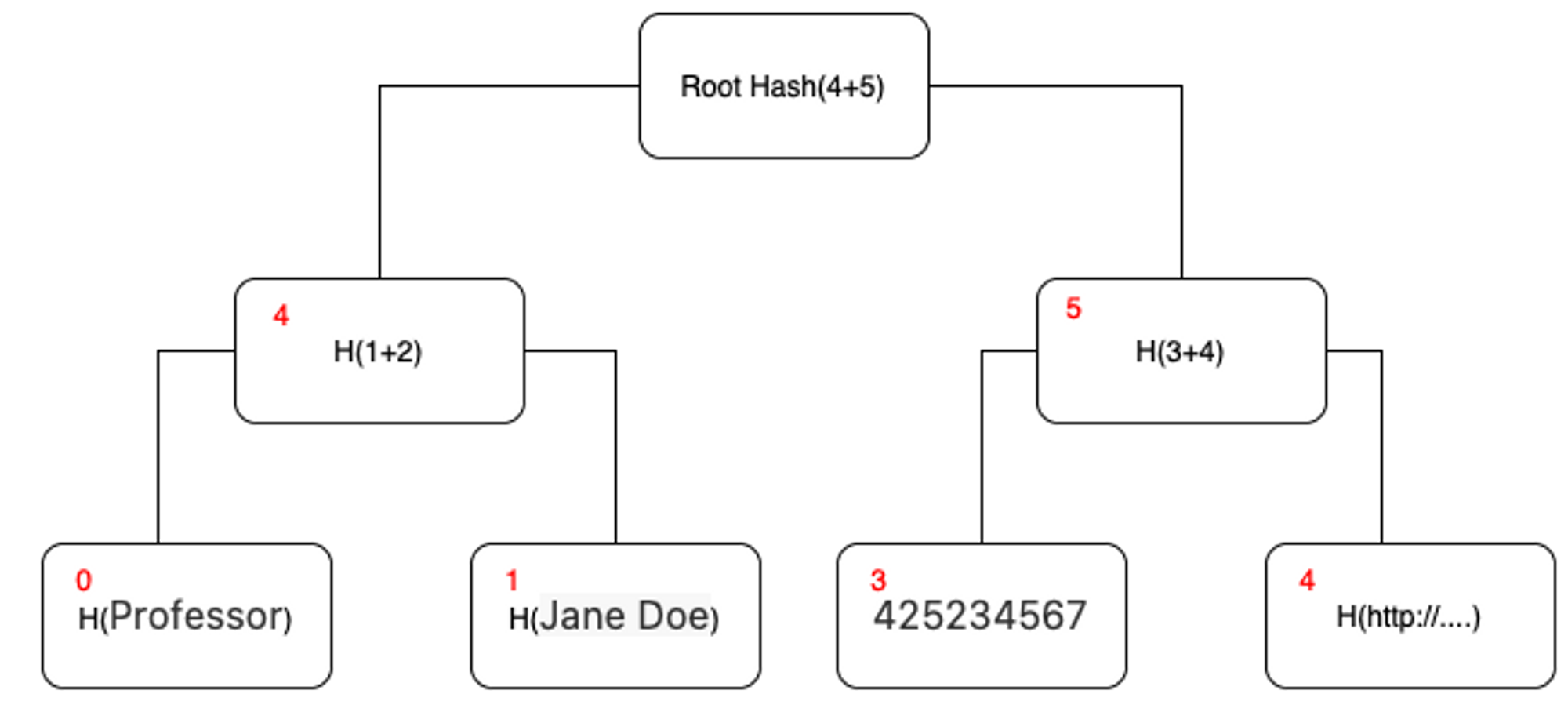
Consider the following JSON-LD document as an example:
{
"@context": "http://schema.org/",
"@type": "Person",
"name": "Jane Doe",
"jobTitle": "Professor",
"telephone": "(425) 123-4567"
}After expanding and canonicalizing the JSON-LD document, we obtain the list of RDF Quads. The key-value pairs derived from these RDF Quads can be represented in the following table:
| Path | Value |
|---|---|
| http://schema.org/jobTitle | Professor |
| http://schema.org/name | Jane Doe |
| http://schema.org/telephone | (425) 123-4567 |
| http://www.w3.org/1999/02/22-rdf-syntax-ns#type | http://schema.org/Person |
Following the extraction of key-value pairs from the RDF Quads, we construct a Merkle tree using these pairs. For each key-value pair, the key is hashed using the designated message digest algorithm to obtain the path in the Merkle tree. The value is also hashed using the same algorithm, and the resulting hash serves as the value of the corresponding leaf node in the tree.
The following image represents the resulting Merkle tree constructed using the hashed paths and values derived from the key-value pairs in the table above: